DKIM, DMARC and SPF: The protective shield for your email communication 🛡️
Protect your email communication! Find out how DKIM, DMARC and SPF protect against spoofing and phishing. 🌐

Email communication is an indispensable part of our daily lives, both professionally and privately. But precisely because emails are so widespread, they are also a popular target for cyberattacks. To protect email users from phishing, spoofing and other threats, there are mechanisms such as DKIM, DMARC and SPF. But how exactly do these technologies work? And what do they actually protect against?
The background to DKIM, DMARC and SPF 📧
To understand why DKIM, DMARC and SPF are so important, let's take a brief look at the problem they are designed to solve. Emails can be spoofed relatively easily because the Simple Mail Transfer Protocol (SMTP), the underlying protocol for sending emails, has no built-in authentication. As a result, attackers can make emails look like they come from trusted senders, when in fact they come from a completely different source.
This is where DKIM, DMARC and SPF come into play. These technologies complement SMTP and provide additional layers of authentication and validation to verify the authenticity of emails.
SPF: The gatekeeper for your domain 🧑✈️
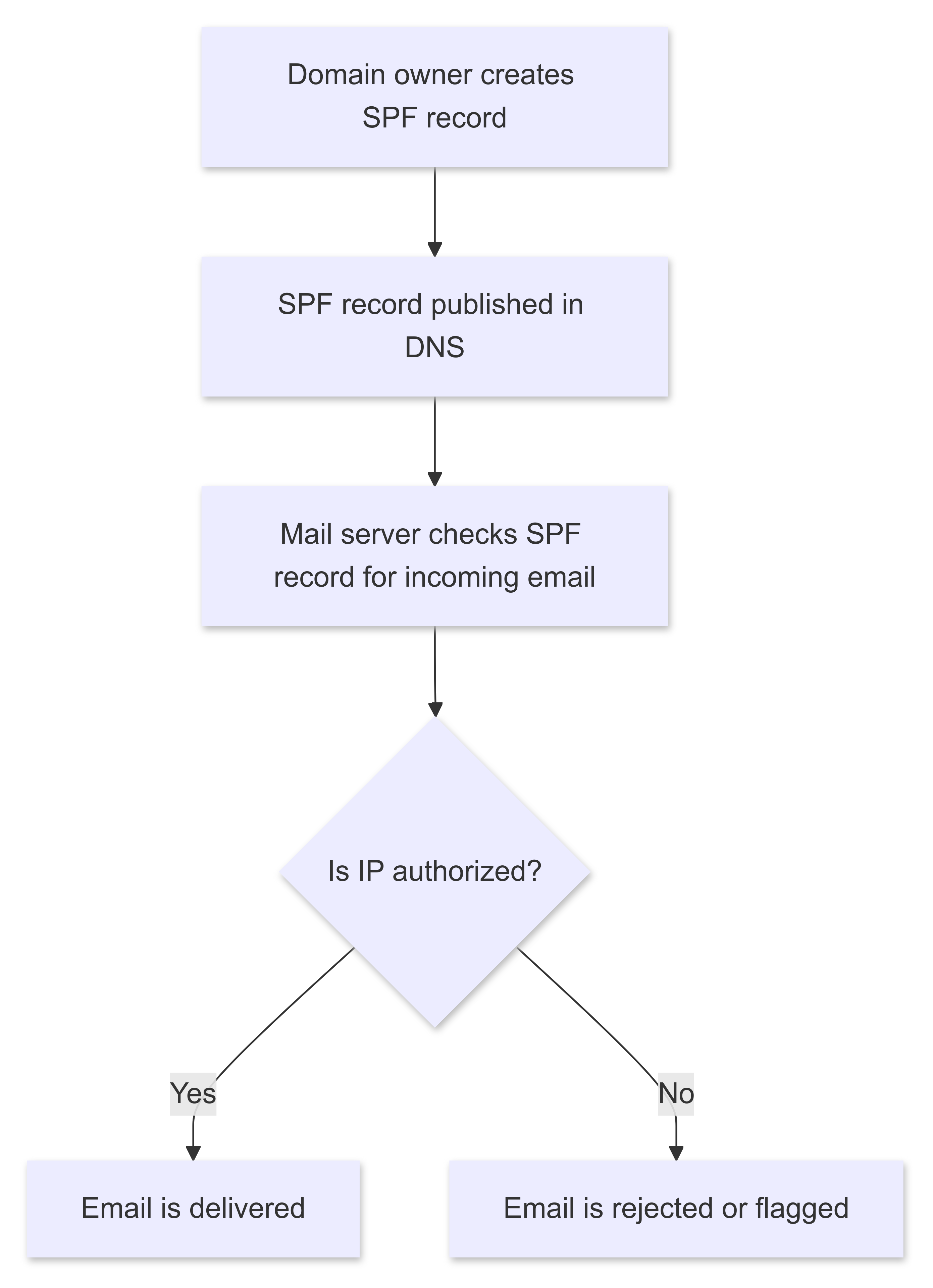
Sender Policy Framework (SPF) is a method for authenticating email senders. It allows the owner of a domain to specify which IP addresses are authorized to send emails on behalf of this domain. This allows recipients to check whether an incoming email actually comes from an authorized server.
How SPF works:
- The domain owner publishes an SPF record in the DNS (Domain Name System) of their domain. This record contains a list of IP addresses or networks that are authorized to send emails for this domain.
- When an email arrives, the receiving mail server checks whether the IP address of the sending server is contained in the domain's SPF record.
- If the IP address is authorized, the email is delivered. If it is not authorized, the email may be rejected or marked as potential spam.
Mermaid diagram: SPF
DKIM: The digital signature of your emails ✍️
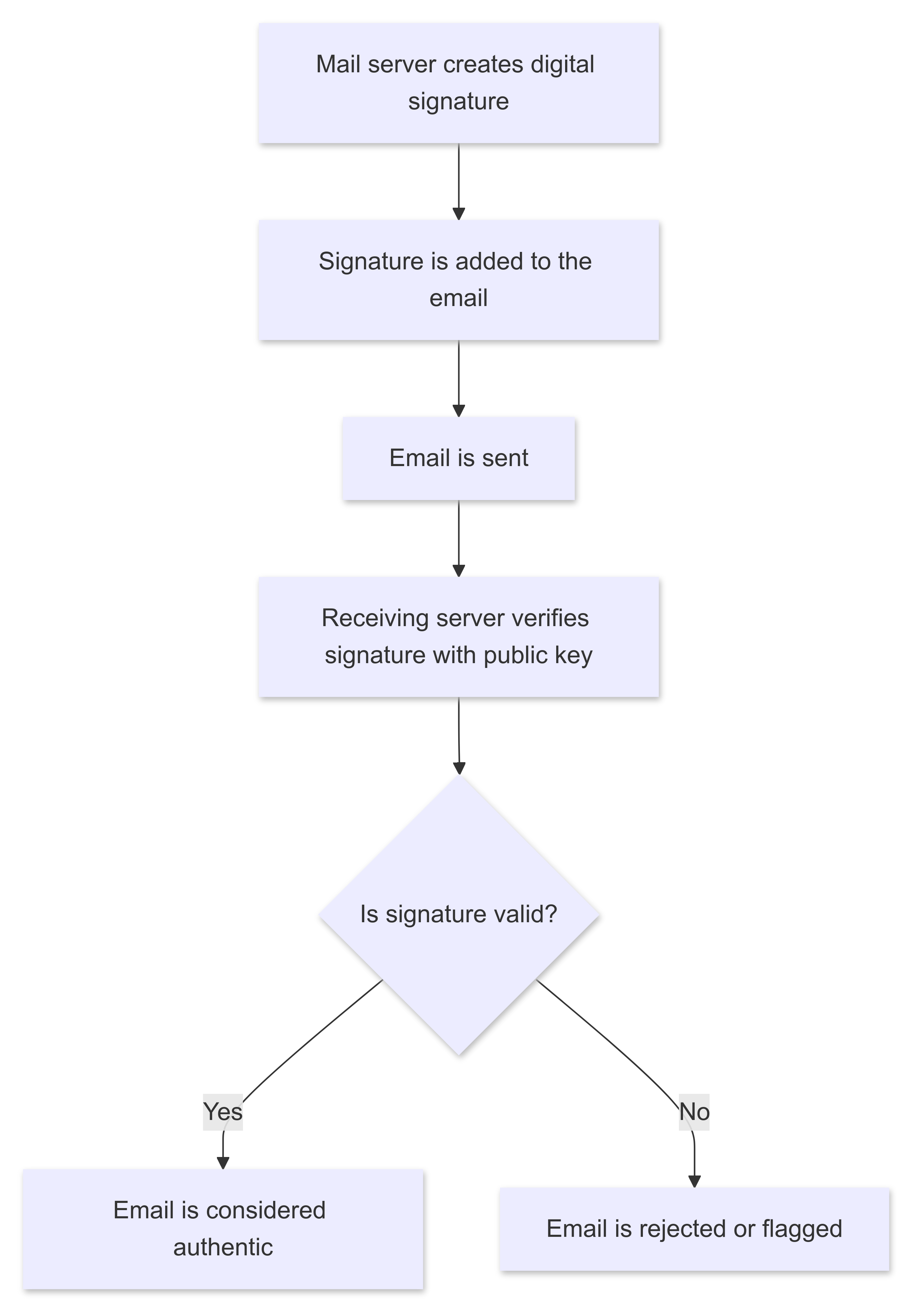
DomainKeys Identified Mail (DKIM) provides a method to ensure that an email has not been tampered with during transmission. Every outgoing email is provided with a digital signature that can be verified by the receiving server.
How DKIM works:
- The sending mail server adds a digital signature to the email. This signature is based on a private key that is only known to the domain owner.
- The receiving mail server can verify this signature with a public key that is published in the domain's DNS.
- If the signature is valid, it is assumed that the email is unchanged and actually originates from the specified domain.
Mermaid diagram: DKIM
DMARC: The director of your email authentication 🎬
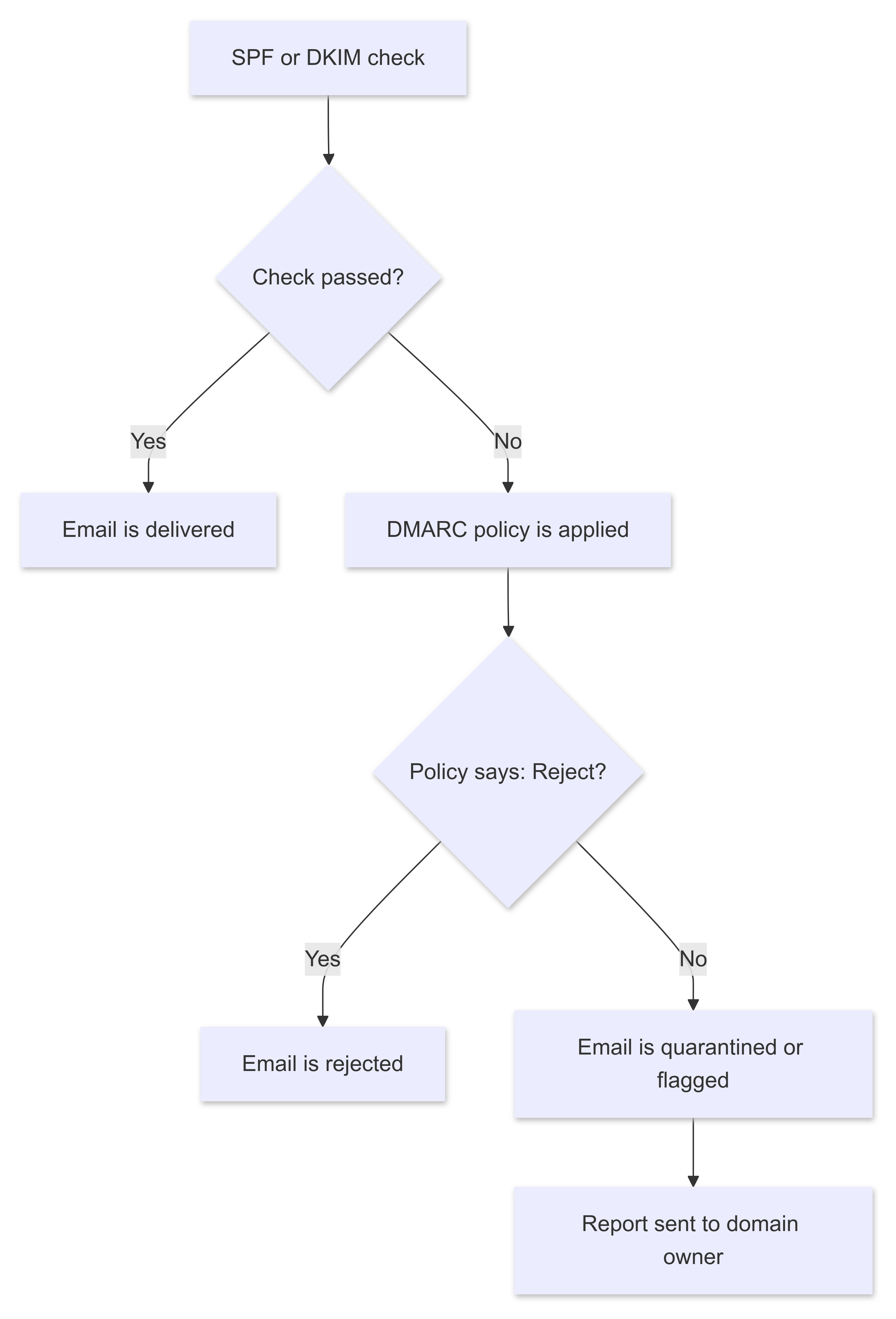
Domain-based Message Authentication, Reporting & Conformance (DMARC) builds on SPF and DKIM and allows domain owners to set policies on how invalid emails should be handled. In addition, DMARC provides a reporting function that allows domain owners to gain insight into abusive email activity.
How DMARC works:
- The domain owner publishes a DMARC policy in the DNS that states how emails that do not pass the SPF or DKIM check should be handled (e.g. reject, move to quarantine, etc.).
- When an email is received, the receiving server checks both the SPF and DKIM checks.
- According to the DMARC policy, the email is either delivered, moved to quarantine or rejected.
- The receiving server sends regular reports to the domain owner to inform them of potential abuse.
Mermaid diagram: DMARC
Anlage in the DNS server 🌐
In order to use DKIM, DMARC and SPF effectively, these mechanisms must be configured correctly in the DNS server. Here is a brief guide on how this works for each of the technologies, including practical examples.
Create SPF record in DNS 🔧
An SPF record is a TXT record that is created in your domain's DNS. This record contains a list of IP addresses or servers that are authorized to send emails on behalf of your domain.
Example of an SPF record:
v=spf1 ip4:192.0.2.0/24 include:spf.example.com -all
Explanation:
v=spf1: Specifies that this is an SPF record.ip4:192.0.2.0/24: Allows all IP addresses in the range 192.0.2.0 to 192.0.2.255.include:spf.example.com: Also allows the servers defined in the SPF records of the domainexample.comto send emails on behalf of the domain.-all: Means that all servers not listed should be considered unauthorized.
Create DKIM record in DNS ✍️
For DKIM, you need a TXT record that is created for a specific selector and the domain. This selector is used in the signature of the email to find the corresponding public key in the DNS.
Example of a DKIM record:
s1._domainkey.example.com IN TXT "v=DKIM1; k=rsa; p=MIGfMA0G...AB"
Explanation:
s1: The selector that is used when creating the DKIM signature._domainkey: A fixed component of the DKIM record.example.com: Your domain.v=DKIM1: Indicates that this is a DKIM record.k=rsa: Indicates that the key is an RSA key.p=MIGfMA0G...AB: The public key that is published in the DNS.
Create DMARC record in DNS 🛡️
A DMARC record is also a TXT record in DNS and specifies how emails that do not pass the SPF or DKIM check should be handled. It also specifies where reports should be sent.
Example of a DMARC record:
_dmarc.example.com IN TXT "v=DMARC1; p=reject; rua=mailto:[email protected]; ruf=mailto:[email protected]; fo=1"
Explanation:
v=DMARC1: Specifies that this is a DMARC record.p=reject: Specifies that all emails that do not pass the checks should be rejected.rua=mailto:[email protected]: Specifies the email address to which aggregated reports should be sent.ruf=mailto:[email protected]: Specifies the email address to which forensic reports should be sent.fo=1: Requests reports for each individual message that fails the check.
What do DKIM, DMARC and SPF protect against? 🛡️
DKIM, DMARC and SPF protect against a variety of attacks based on spoofed sender addresses:
- Phishing: Attackers attempt to steal sensitive information by impersonating trusted senders.
- Spoofing: Attackers pretend to send emails from a legitimate domain in order to deceive the recipient.
However, these mechanisms do not prevent emails from being sent from legitimate servers but containing malicious content (e.g. malware). Nor can they prevent emails from being sent from a compromised legitimate account.
Conclusion 🎉
DKIM, DMARC and SPF are essential tools for ensuring the security and integrity of email communication. They ensure that emails actually originate from the specified sender and have not been manipulated en route. However, they are not a panacea and should always be used in the context of other security measures.
Do you have any questions about DKIM, DMARC or SPF? Leave a comment below!
